Project Cracks Vault PIN with Brute Force
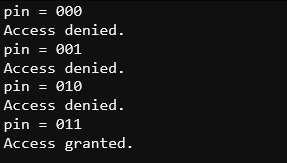
A PIN with three binary digits has 8 possible combinations: 000, 001, 010, 011, 100, 101, 110, and 111. With that number, it’s not too time-consuming to brute force attack manually. Just hand-enter all the combinations and within a minute, you’ve got access.
With more possible digits, a PIN could end up taking hours, days, or even years to crack with brute force by hand. So, brute force attacks are often mounted by projects—the attacker doesn’t have to spend all that time manually typing in different PIN values. The computer (or in our case, the micro:bit module) does the work, and the attacker can check back periodically to find out if the PIN has been cracked.

Transmitter project: bank_vault_crack
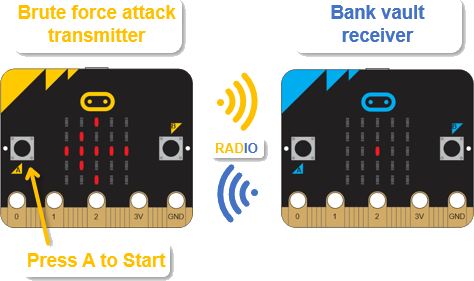
The Bank Vault Receiver micro:bit should still be on and running the bank_vault_receiver project.
- Enter and flash bank_vault_crack into the PIN Pad Transmitter micro:bit.
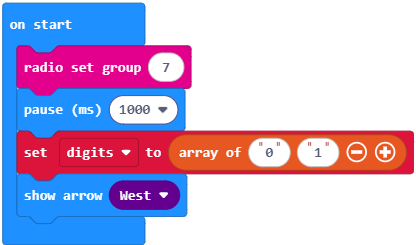
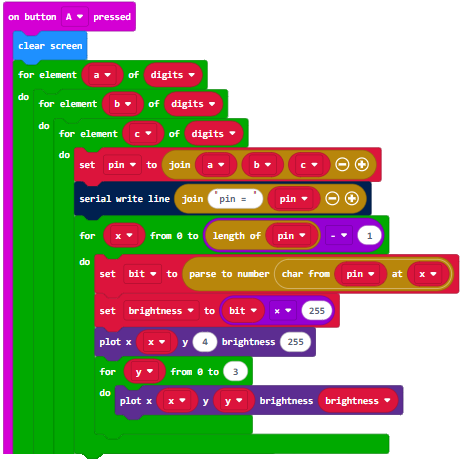
- Press the PIN Pad Transmitter micro:bit’s A button to start the brute force attack.
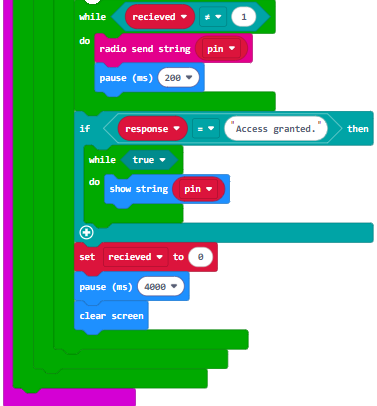
- Watch the PIN Pad Transmitter micro:bit’s display as it cycles through all eight combinations of the brute force attack.
- Verify that the project figures out the correct 011 PIN for gaining access and shows it with show string.
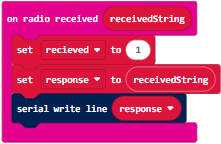
- Open a terminal in a browser that’s connected to the PIN Pad Transmitter micro:bit.
- Press/release the PIN Pad Transmitter micro:bit’s reset button and monitor the terminal activity.
See how it keeps trying combinations until it reaches the correct 011 PIN?