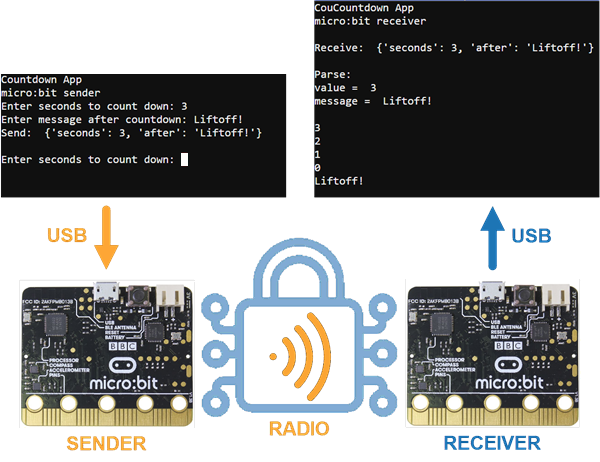
What It’s about
Sniffing is the act of silently monitoring communication. Some sniffing is not considered a cyber attack. For example, law enforcement agencies and/or network administrators might monitor network communication. However, cyber attackers use sniffing to gain access to data like passwords and personal information, which they might use to gain access to personal accounts, networks, and other resources.
Not all people or devices are careful about encrypting data, which makes it very easy for cyber attackers to “sniff” private data. For example, when step counters were new, not all brands encrypted their data. At one marathon race, attackers waited at the finish line and collected hundreds of usernames and passwords.
This activity has examples for examining how data can be vulnerable to sniffing attacks and demonstrates how encryption is the first line of defense against those attacks.
Before you start
Make sure you have:
- Two or more micro:bit modules (on or off a cyber:bot)
- One cyber:bot, fully assembled and tested (optional)
- Two or more USB A to MicroB cables
- Two or more computers with access to the python.microbit.org editor.
Complete these tutorials first:
After you finish
You will be able to add simple encryption to just about any of your micro:bit radio applications and you will be ready to move on to these tutorials (coming soon!)
You will also be one step closer to ready to compete in cybersecurity contests such as Hackers vs. Defenders.
